Regular, Structured Security Audits for IT Departments and IT Managers
This software solution supports IT departments and IT managers in small, medium-sized, and large organizations in conducting IT security audits. It combines internal endpoint scans, external attack surface analyses, and automated remediation measures to systematically identify vulnerabilities and—where possible—eliminate them.
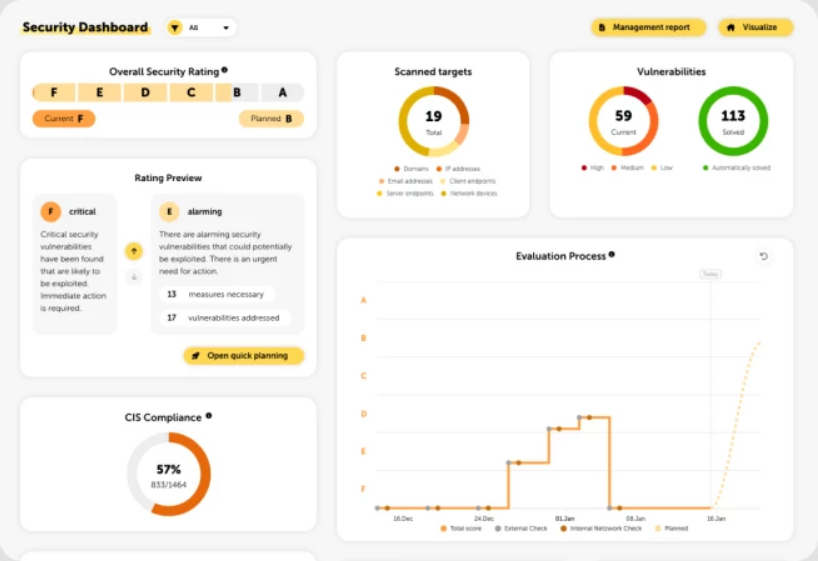
Agent-Check (Windows Endpoint)
Analysis of vulnerabilities, outdated software, and security-relevant configurations using locally installed endpoint agents.
External Check
Assessment of publicly accessible systems such as IP addresses, domains, and mail servers for potential attack vectors.
Network Check
Detection and evaluation of devices within the internal network, regardless of operating system.
- Summary assessment of the current security status
- Historical graphs to track changes over time
- Overview of particularly high-risk systems and topic areas
- Resolution of common vulnerabilities on endpoints and systems through automated processes
- Control via schedules, device groups, and update categories
- Reduction of manual work for standardized tasks
- Prioritization of identified vulnerabilities based on urgency
- Automatically generated action plan for structured resolution
- Support for technical implementation and internal communication
- Management report with a compact overview
- Technical report with detailed information for IT professionals
- Simplified visualizations to support internal coordination
- Scalable for different company sizes and structures
- Time savings through automation of recurring audit processes
- Standardized results for documentation and comparability
- Improved traceability for both internal and external stakeholders
- Support in meeting compliance requirements (e.g., NIS2, ISO 27001)
- Internal IT departments in companies and public institutions
- IT managers, security officers, and IT leadership
- Organizations with legal or industry-specific requirements
- Processing of personal data in accordance with GDPR
- Data storage and processing exclusively within the EU
- No external access to internal systems; execution via locally installed endpoint agents or network gateways
- Software-as-a-Service with monthly or yearly licensing
- Interfaces to existing systems such as helpdesk or monitoring
- Option for a non-binding demonstration or trial period
The software solution enables IT departments to conduct security audits in a structured, traceable, and partially automated manner. It serves as a tool for internal security strategies and supports compliance with external requirements.
